For the first time in 13 years, the U.S. Nuclear Regulatory Commission has updated its guide on protecting nuclear plants from cyber attacks. In the newly re-worked 160 pages, the organization has outlined details around topics such as inspections and has added a requirement for nuclear plants to submit cybersecurity plans. This initiative was likely prompted by the expanding threat landscape facing critical infrastructure, which largely stems from vulnerabilities in OT. In this piece, we check in on the reports forecasting the challenges we can continue to expect in the OT realm.
A Ransomware Storm
One threat that we can definitely expect to see for some time in the forecast is the threat of ransomware. According to research reflected in Dragos’ “ICS/OT Cybersecurity Year in Review 2022” report, ransomware attacks targeting industrial organizations have increased by 87%. The company tracked 605 cases in 2022 alone. For instance, there were “several Conti victims in the automotive industry in 2022, as well as multiple LockBit variants affecting victims in sectors like construction, electric and manufacturing,” TechTarget explains in its coverage of the report. As such, the OT cybersecurity market is predicted to become even more dominant.
Taking Shelter with Cybersecurity Investments
Considering the risks, OT-based industries are having to prioritize cybersecurity in their investments. Take the rail industry for example. With the rise in OT’s convergence with IT, rail and transit operators are forced to acknowledge an evolving environment that comes with flaws. In turn, ABI Research projects that cybersecurity spending in the rail sector will reach $300 million globally by 2027. This may receive an even bigger boost by growing regulatory trends, as Help Net Security points out.
Parting of the Clouds: Cybersecurity Solutions
There are several solutions that organizations can explore in order to protect their facilities. One suggestion that Thomas Zhang, security analyst at Orange Cyberdefense, poses an argument for is the use of deception techniques. While typically an IT approach, deception essentially allows organizations to detect suspicious activity, mislead bad actors and collect important information. However, “It is almost impossible to have a deception technology that can be applied to all industrial control devices,” writes Zhang in The Hacker News. Therefore, customization can be an issue.
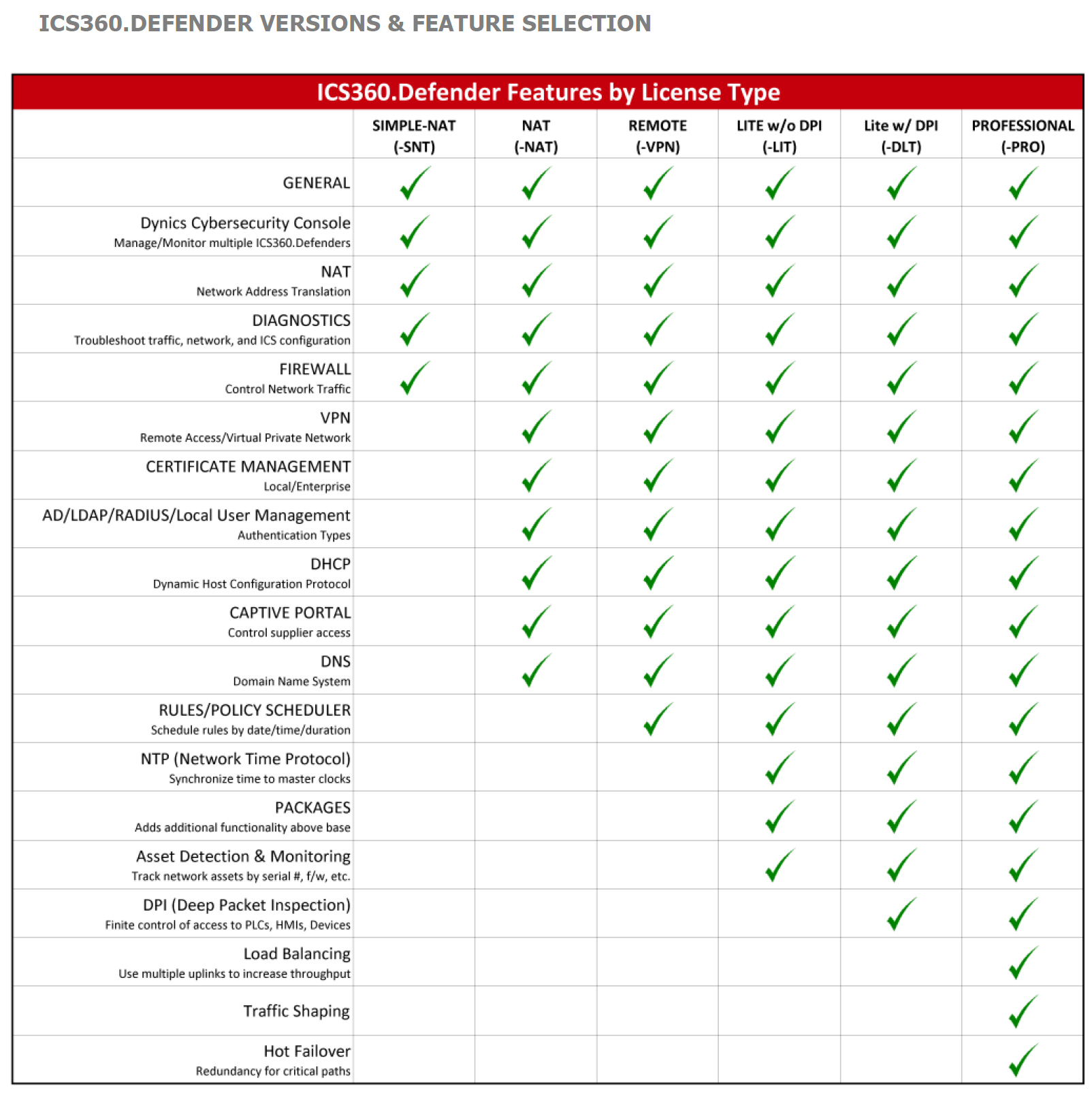
Additionally, there are more proven cybersecurity methods such as integrating an asset management system that monitors data flows, which DYNICS can assist with our suite of cybersecurity solutions.
Sources:
- “NRC issues first update of 2010 regulatory guide to strengthen cybersecurity at nuclear plants” – Stephen Singer, Utility Dive
https://www.utilitydive.com/news/nrc-cybersecurity-update-guide-nuclear-plants/642542/ - “Dragos: ICS/OT ransomware attacks up 87%” – Alexander Culafi, TechTarget
https://www.techtarget.com/searchsecurity/news/365531080/Dragos-ICS-OT-ransomware-attacks-up-87 - “Inadequate cybersecurity investments leave rail industry at risk” – Help Net Security
https://www.helpnetsecurity.com/2023/02/09/rail-industry-cybersecurity-spending/ - “Honeypot-Factory: The Use of Deception in ICS/OT Environments” – Thomas Zhang, The Hacker News
https://thehackernews.com/2023/02/honeypot-factory-use-of-deception-in.html