Operational Technology (OT) environments are fundamentally different from traditional IT systems. While “detect and respond” may be a familiar mantra in IT cybersecurity, it doesn’t translate to OT. To truly protect physical systems, organizations must shift toward prevention and control before impact, not retrospective detection after the fact.
1. Detection in OT Is Too Slow and Too Uncertain
In many high-profile breaches, professionals have struggled to agree with what happened, let alone when or how it started.
As Greg Jenkins, Sales Leader at DYNICS, puts it:
“Three top-tier organizations, three different detection lenses, three different conclusions weeks after the event.”
If experts can’t reach consensus on an incident after the fact, expecting real-time detection to reliably stop a physical impact is unrealistic.
A key technical challenge is that most OT devices are legacy systems built for reliability and uptime, not security. They lack the processing power or architectural hooks required for traditional threat detection tools like IT endpoint detection and response (EDR) or anomaly detection systems to work reliably. In fact, many academic studies show that anomaly detection models, even those touted as advanced, can perform well in tests but fail to detect unknown or novel attacks in real environments, sometimes catching fewer than 15% of threats they weren’t specifically trained on (Kus, D., Wagner, E., Pennekamp, J., Wolsing, K., Fink, I. B., Dahlmanns, M., Wehrle, K., & Henze, M. (2022, May 18)).
OT systems also run continuously; any scanning or heavy monitoring can disrupt operations, meaning detection tools often operate at a distance or passively, long after a threat has entered the system. (C. Kerry Nemovicher, 2025)
2. The Physical Stakes in OT Make Response Too Late
In IT, delayed detection can mean lost data and while serious, data loss does not usually cause safety incidents. In OT, a breach before detection can result in production halts, safety failures, environmental damage, or physical destruction. The ransomware attack on Colonial Pipeline in 2021, notorious for disrupting fuel delivery, illustrates how OT impacts extend well beyond digital assets.
Even frameworks like NIST recognize detect as a separate function in cybersecurity frameworks, but the industry’s focus on detection and response remains skewed toward IT and retrospective analysis, not forward-looking prevention in OT environments. (J. Benjamin, 2021)
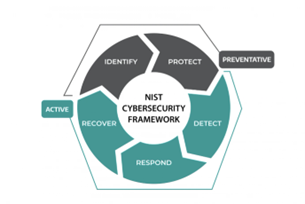 NIST Cybersecurity Framework (Dragos.com)
NIST Cybersecurity Framework (Dragos.com)
OT environments often employ legacy protocols that intrusion detection systems (IDS) or endpoint detection and response systems (EDRs) don’t understand. Without deep protocol awareness, alerts are noisy, ambiguous, or meaningless, making detection ineffective (https://www.nozominetworks.com/, 2026).
3. OT Must Focus on Control and Prevention Before Execution
This is why OT security cannot depend on attribution, alerts, or after the fact detection. Instead, resilience must be built into what systems are allowed to do, and what they are not allowed to do, before issues arise.
Key pillars of effective OT cybersecurity include:
- Strict asset governance and segmentation: You can’t protect what you don’t know you have. End-to-end, OT-aware asset inventories and segmentation limit attack paths. (https://www.networkcritical.com, 2026)
- Zero-trust controls and least privilege policies: Assume you will be breached. Limit the potential for lateral movement. (https://www.fortinet.com/, 2026)
- Preventive control of actions, not just watching for anomalies: Control logic and commands should be validated at their source based on allowed behaviors, not just logged and “flagged” later.
As Greg Jenkins notes:
“OT security can’t depend on attribution or alerts. It has to be about controlling what systems are allowed to do before something bad happens.”
In OT, protection trumps detection not because detection isn’t valuable, it’s that detection alone is too slow, too incomplete, and too prone to uncertainty to prevent physical consequences.
Conclusion: Why Now Is the Time for ICS360.Defender
 Given these realities, organizations must move beyond classic detection-centric models to solutions built specifically for OT contexts: lightweight, preventative controls that enforce safe system behavior before execution, not after attack signals appear.
Given these realities, organizations must move beyond classic detection-centric models to solutions built specifically for OT contexts: lightweight, preventative controls that enforce safe system behavior before execution, not after attack signals appear.
For organizations looking to truly protect industrial operations and safeguard physical processes, consider ICS360.Defender, a system designed around OT-centric prevention and control, not legacy IT detection logic. In a world where milliseconds can mean safety or catastrophe, protect first, detect second isn’t just smarter, it’s essential.
Sources:
Kus, D., Wagner, E., Pennekamp, J., Wolsing, K., Fink, I. B., Dahlmanns, M., Wehrle, K., & Henze, M. (2022, May 18). A false sense of security? revisiting the state of machine learning-based industrial intrusion detection. arXiv.org. https://arxiv.org/abs/2205.09199
The OT Industry’s Cybersecurity Crisis: Why Detection Is So Challenging By C. Kerry Nemovicher
https://www.cryticasecurity.com/blog/the-ot-industry-cybersecurity-crisis-why-detection-is-so-challenging
Correcting Prevention Bias in Your OT Cyber Incident Response By Jacob Benjamin
https://www.dragos.com/blog/correcting-prevention-bias-in-your-ot-cyber-incident-response
How Are OT and IT Cybersecurity Difference?
https://www.nozominetworks.com/cybersecurity-faqs/how-are-ot-and-it-cybersecurity-different
OT Cybersecurity: Safeguarding the Systems that Run Our World
https://www.nozominetworks.com/cybersecurity-faqs/how-are-ot-and-it-cybersecurity-different
5 Best Practices For Operational Technology (OT) Security
https://www.fortinet.com/resources/cyberglossary/ot-security-best-practices