The New Reality of Operational Technology
Operational Technology (OT) environments are no longer isolated systems humming quietly on the factory floor. With the rise of industrial connectivity, cloud analytics, and IT/OT convergence, they’ve become part of a much larger digital ecosystem.
Yet, many organizations are still managing their industrial networks with siloed tools, one system for visibility, another for firewalling, and a third for user access control. This patchwork approach leaves critical blind spots and increases operational complexity.
Today, the need for integrated security, visibility, and control isn’t optional, it’s essential for protecting up time, ensuring safety, and maintaining resilience in modern industrial networks.
Visibility: The First Step Toward Security
You can’t protect what you can’t see. In many industrial environments, as much as 30–50% of assets remain unknown or unmanaged, according to the 2024 Dragos Industrial Cybersecurity Report. These unmonitored devices can include outdated PLCs, unauthorized laptops, or vendor-installed components that quietly communicate across your network.
Without comprehensive visibility into every connection, traffic pattern, and data flow, teams are forced into reactive security, discovering problems only after downtime or compromise occurs.
Modern OT networks require real-time asset discovery and network mapping that extends deep into the protocol layer. Deep Packet Inspection (DPI) across Modbus, Profinet, Ethernet/IP, and other industrial protocols is critical for identifying anomalies before they escalate.
The takeaway: Visibility forms the foundation of both security and control. It’s not a luxury; it’s a necessity.
Security: Defending the Industrial Edge
Cyber threats targeting OT have become more frequent and more sophisticated. The 2024 IBM X-Force Threat Index reported a 40% increase in ransomware attacks on critical infrastructure, many of which started with lateral movement between IT and OT systems. Traditional perimeter firewalls weren’t designed for this environment; industrial networks need embedded security at every layer.
Effective OT defense requires:
- Micro-segmentation to isolate traffic and prevent lateral movement
- Protocol-aware firewalls that understand industrial commands
- Secure remote access to control third-party and vendor connections
When these capabilities operate in isolation, incident response becomes fragmented. But when they’re integrated, they form a defense-in-depth strategy that scales across the enterprise.
Control: Centralization Drives Efficiency
Security and visibility are powerful, but without control, they remain passive. Centralized management gives OT teams the ability to enforce consistent policies, respond quickly, and optimize system performance without interrupting production.
Organizations with centralized network control have been shown to reduce downtime by 27% and cut remediation time by half (ARC Advisory Group, 2023). With unified management, configuration updates, firmware changes, and security policies can be deployed consistently from a single console.
That’s the difference between reacting to alerts and orchestrating a secure, predictable network environment.
Integration: One Platform, Unified Purpose
The real power lies in bringing these elements together—visibility, security, and control—into a single, integrated ecosystem.
According to SANS Institute’s 2024 ICS Survey, 90% of OT leaders cite integration as their top security investment priority. Why? Because a unified platform reduces silos, simplifies compliance, and delivers a measurable return on security investment.
Integrated systems streamline:
- Threat Protection: OT Teams need to focus on running the plant. Protection led tools stop unauthorized, and malicious traffic.
- Incident response: Coordinating actions automatically across OT lines, cells and endpoints
- System management: Reducing complexity and manual effort
Integration isn’t just about tools working together, it’s about people, processes, and technology sharing a common operational picture.
The Future of OT Cybersecurity
As digital transformation accelerates, industrial networks are expected to meet the same cybersecurity standards as IT systems. Gartner predicts that by 2027, 60% of OT environments will integrate IT-level visibility and security controls. Emerging frameworks like NIST 800-82 and CISA’s Secure by Design initiative reinforce this direction, emphasizing resilience through integration and automation.
Looking ahead, AI-driven analytics, software-defined networking (SDN), and adaptive trust models will continue to shape the next phase of OT security. But no matter how advanced technology becomes, the foundation remains the same: integration enables insight, insight enables action, and action sustains security.
ICS360 Powered by DYNICS: Unified Security, Visibility, and Control for OT
 The ICS360 Suite by DYNICS was designed to meet these needs: to bring industrial organizations a unified platform that bridges security, visibility, and control.
The ICS360 Suite by DYNICS was designed to meet these needs: to bring industrial organizations a unified platform that bridges security, visibility, and control.
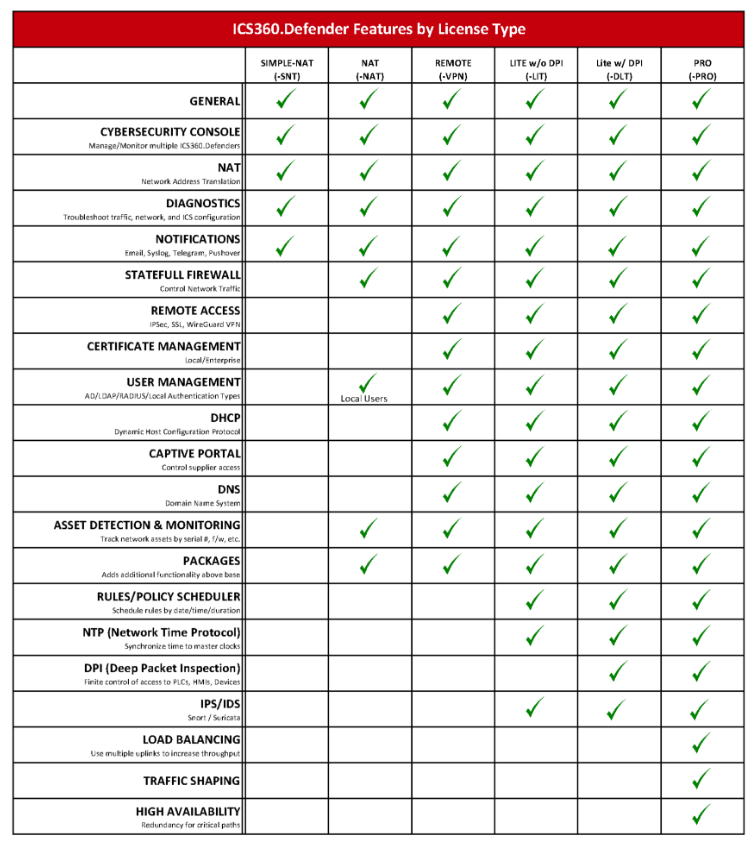
- ICS360.Defender – Delivers real-time threat Protection, threat detection, Deep Packet Inspection (DPI), firewalling, and secure remote access at the OT network edge.
- ICS360.DCC – Offers centralized visibility and command for distributed large scale management of the platform.
- ICS360.IAM – Provides user identity and access management purpose-built for industrial environments.
- OT-SDN Controller – Enables software-defined networking and intelligent micro-segmentation for scalable control, with an intuitive interface designed for OT.
- ICS360.FlexConnect Switches – Hardened Layer 2, Layer 3, and SDN industrial switches designed for reliable connectivity and data flow management.
- ICS360.Fusion – Integrates and visualizes security, performance, and operational data into one comprehensive view.
Together, these solutions form one unified OT Security and Data Suite; a scalable foundation for protecting critical infrastructure while enabling operational excellence.
Final Thoughts
In today’s interconnected industrial world, visibility reveals the threats, security defends the edge, and control empowers response, but integration ties it all together. With the DYNICS ICS360 Suite, organizations can finally unify these pillars under one platform, simplifying management, strengthening protection, and unlocking the true potential of secure, data-driven operations.
Sources:
Operational Technology (OT) and IoT Security – Gartner
https://www.gartner.com/en/conferences/apac/security-risk-management-australia/featured-topics/operational-technology-iot-security#:~:text=Expert%20insights%20on%20securing%20OT,in%20a%20hyper%2Dconnected%20world
SANS 2024 State of ICS/OT Cybersecurity – Written by Jason D. Christopher, Foreword by Tim Conway
https://sansorg.egnyte.com/dl/oq4USL3qoA
Key Technology Trends for 2023 – By Craig Resnick
https://www.arcweb.com/industry-best-practices/key-technology-trends-2023
X-Force Threat Intelligence Index 2024 reveals stolen credentials as top risk, with AI attacks on the Horizon – By Charles Henderson
https://www.ibm.com/think/x-force/2024-x-force-threat-intelligence-index
Dragos Reports OT/ICS Cyber Threats Escalate Amid Geopolitical Conflicts and Increasing Ransomware Attacks – Dragos, Inc.
https://www.dragos.com/resources/press-release/dragos-reports-ot-ics-cyber-threats-escalate-amid-geopolitical-conflicts-and-increasing-ransomware-attacks