At the beginning of May, the NSA and CISA released an urgent warning regarding pro-Russian hacktivists targeting OT networks and monitoring systems throughout the U.S. and Europe. In a fact sheet co-authored by the FBI, Environmental Protection Agency, Department of Energy, United States Department of Agriculture, Multi-State Information Sharing and Analysis Center, the U.K. National Cyber Security Centre, and the Canadian Centre for Cyber Security, the agencies outline steps critical infrastructure operators should take, including “hardening human machine interfaces, limiting exposure of OT systems to the internet, using strong and unique passwords, and implementing multifactor authentication for all access to the OT network.” But, there is one recommendation we would add – control your network.
The Importance of Controlling Your Network
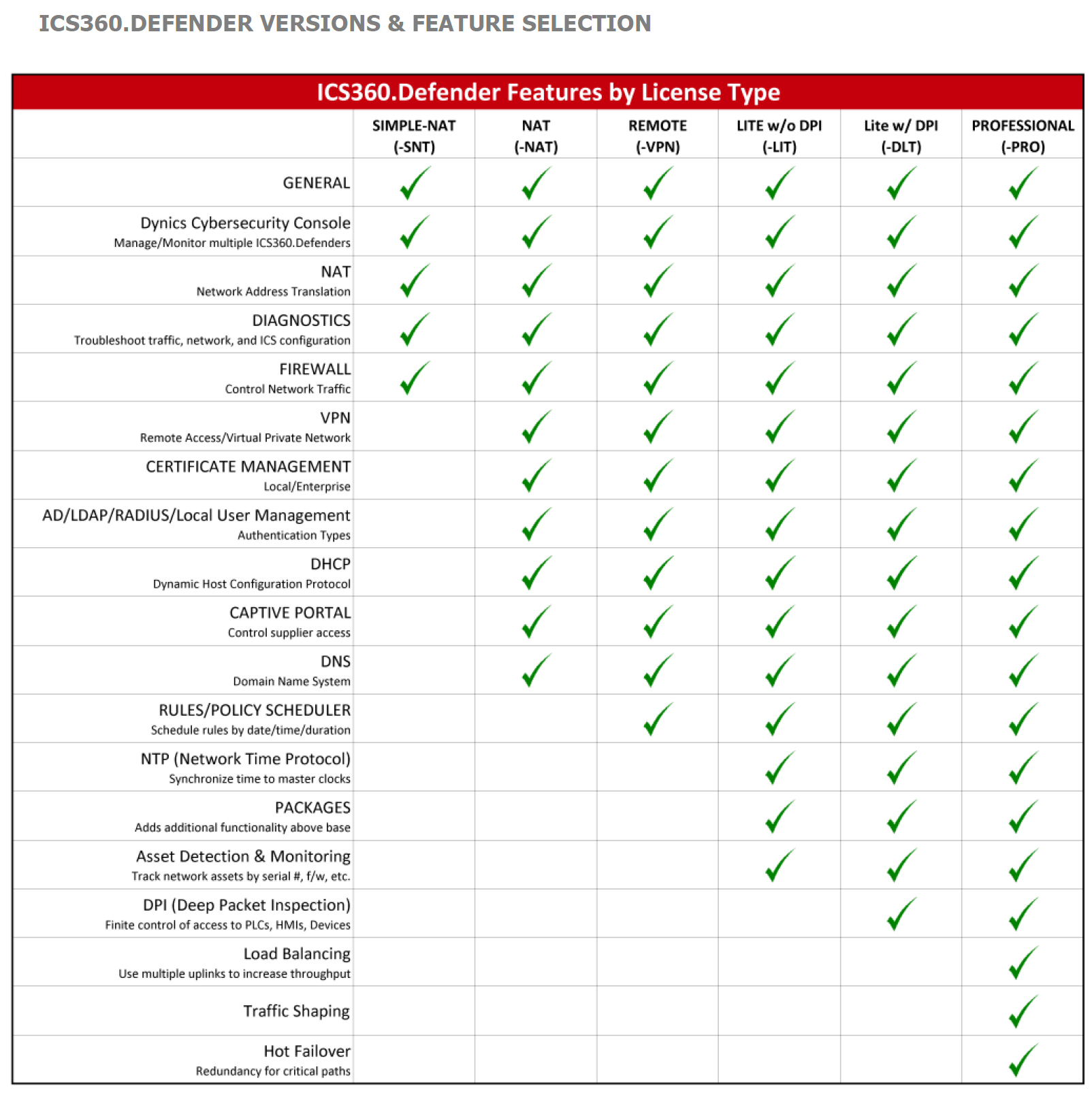
In our latest industry interactions, including a symposium and multiple meetings with end users and reseller partners, control has been an essential topic. Those we convene with often share how inefficient trying to protect OT networks by keeping up with threats and vulnerabilities can be. That’s because that is still a very defensive or reactionary approach. Having control allows you to take an offensive, preventative approach. If you understand what’s on your network, what communication flows you have, and what is necessary to maintain operations, you can remove the risk and protect the network while keeping the plant running. Having an easy-to-use, corresponding suite of tools designed to work together can help you to achieve this.
The Importance of Having the Right Conversations
DYNICS offers such a suite of tools that have been developed around a control-first mindset, but we have been able to get to that point because we focus on the end users actually responsible for seeing the day-to-day execution of them. While we are obviously concerned with cybersecurity, which recent events such as the hacktivist case reflect, we know that such lofty topics and conversations aren’t actually effective if operators themselves still do not thoroughly understand how to address them. Rather than attending an event like RSA, our team chose to go to Chicago instead. While there, we connected with manufacturers directly to discuss the challenges they face in control implementation and what would help. Rather than selling cybersecurity to control teams, we want to meet them where they are at and provide control benefits. By instilling that value first, we then establish a foundation to expand off of to create holistic solutions that eventually block threats from foreign actors all together.
Sources:
- “Urgent Warning from Multiple Cybersecurity Organizations on Current Threat to OT Systems” – National Security Agency
https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-Release-View/Article/3761830/urgent-warning-from-multiple-cybersecurity-organizations-on-current-threat-to-o/